|
“Premise: The Anthrax Mailer is a
major
Virus-Trojan-Worm writer.
Premise: The FBI Behavioral Profile
of the Anthrax Mailer
is accurate.
Then it would follow that the profile
fits the Virus Writer.”
"Usually, older virus writers work as engineers….”
Some worm and virus writers leave
clues to their identities
in their coding or in some aspect of their Modus Operandi
link=bacillus
Anthrax Virus Trojan Worm: Bugs in the Mail

CLICK
"If average Internet users had an inkling of what's out there, they'd
avoid the Web like a subway full of Anthrax."
-Protection Technologist
VIRUS TROJAN WORM MALWARE MALICIOUS SCRIPT SPOOFING PHISHING.....WHATEVER YOU
CALL IT:
Around 92 million people in the US are thought to have received a phishing email
over the past year - and a staggering 30 million have fallen for such a scam, according to a survey to be published by Gartner
on Thursday.
Phishing is an internet scam in which unsuspecting users receive official-looking
emails that attempt to fool them into disclosing online passwords, user names and other personal information. Victims are
usually persuaded to click on a link in an email that directs them to a doctored version of an organisation's website - such
as a fake bank website.
"The Internet is a pretty dirty place," "If you hook up a personal computer to a modem, you have about 20 minutes before something
infects it."
PC viruses spawn
$55 billion loss in 2003
Reuters January 16, 2004, 5:41 AM PT
"Trend Micro, the world's third-largest antivirus software maker, said Friday that computer
virus attacks cost global businesses an estimated $55 billion in damages in 2003, a sum that is expected to increase this
year.
Companies lost roughly $20 billion to $30 billion in 2002 from the virus attacks, up from
about $13 billion in 2001, according to various industry estimates.
"The economic and financial impact of virus attacks will continue to climb in 2004," Lionel Phang,
Trend Micro's managing director told Reuters in an interview. He did not have a forecast for the year.
Spam threats and network viruses will likely become more prevalent this year, he said.
"The spam threat will increase exponentially, and will become the hideouts for viruses and hacking
programs trying to gain an entry into the network," he added.
"Blended threats also will remain the standard way to attack networks, where one virus file will
create four to five different activities within the system."
Phang offered the following example of a blended threat: A spam-generating virus causes a surge in
the company's network traffic and prompts its network administrators to block the junk e-mail, and while technicians try to
fix the spam problem, the virus drops a program into the system that monitors keystrokes and steals company passwords
and user IDs.
Viruses can gain entry into computer networks via instant messaging channels, such as Internet Relay
Chat (IRC) programs and Time Warner's ICQ service, Phang added."
Year 2004 witnesses highest virus outbreak
Monday, 03 January , 2005, 07:43
The
year 2004 has registered the highest number of computer virus outbreak incidences compared to the previous years. A Trend
Micro study has revealed that as many as 30 virus outbreaks marked 2004, and the first quarter alerts numbering 12 in all,
proved to be the highest ever reported in any given quarter in a three-year period range.
The average outbreaks have
only been hovering around 5 in any quarter, but during the first few months of 2004, the number inched close to 45 per cent.
BAGLE, NETSKY and MYDOOM dominated the outbreak scene, causing 25 of the total 30 virus outbreaksThe total number
of infections recorded by the Trend Micro World Tracking Center (WTC) is said to be steadily growing year-on-year.
In
2004, WTC recorded a total of 3.78 lakh infections, up by almost 8 per cent from 2003's 3.51 lakh recorded infections.
The
company documented a total of 16,880 malware detections in 2004. Trojans at 33 per cent of all malware comprised the bulk
of detections.
There were more than 5,000 Trojan detections.
The year also saw an increase in profit-driven
attacks.
Trend Micro documented a total of 2,830 bot programmes, which was more than 35 per cent of the newly discovered
malware detections by the company for the entire year.
Based on the general trend of malicious code and Internet-based
attacks in 2004, Trend Micro anticipates newer and more effective methods of attack in 2005 to ensure greater reach, effectiveness
and larger profits. According to Trend Micro, blended threats, which could compromise and drain network resources considerably
would continue to hound Internet users.
With the foreseen increase in the usage of web traffic, redirection and spoofing
techniques would require more stringent surfing policies. There would be a need for strengthening e-mail- filtering services,
as spam and phishing would continue to cause e-mail glut.
And as the time between vulnerability, discovery and exploit
release narrows down, there would be a need for proactive assessment tools.
"Forget about Pandora's Box.
Opening your web browser these days is like opening Pandora's Warehouse".
-Protection Technologist

"As far as web browsers go,
Microsoft's Internet Explorer is the
viral welcome mat that stands head and shoulders above the rest."
-Protection Technologist


Department of Computer Science, Princeton University
WEB SPOOFING allows an attacker to create a "shadow copy" of the entire World Wide Web. Accesses to the shadow Web are funneled
through the attacker's machine, allowing the attacker to monitor all of the victim's activities including any passwords or
account numbers the victim enters. The attacker can also cause false or misleading data to be sent to Web servers in the victim's
name, or to the victim in the name of any Web server. In short, the attacker observes and controls everything the victim does
on the Web. We have implemented a demonstration version of this attack.
Raging Computer Viruses
TETSUYA YAMAZAKI
Information and communications Research Unit

CODE RED: Malicious programs such as viruses, worms, and Trojan horses are causing increasingly serious damage as they become
more sophisticated year after year and as they spread more quickly via the highly prevalent Internet. This report summarizes
recent trends in computer viruses,with emphasis on the above two viruses.
|
| CLICK FOR LATEST VIRUS INFORMATION |
"How often do you hear people say things like "I haven’t got an antivirus and I have
never been infected by a virus"?
This might just have been possible some time ago, when there were relatively few viruses out and
about. Today however, with more than 70,000 types of malicious code in existence, it is not likely.
One frequent misconception is that virus authors have the exclusive goal of deleting files from the
hard disks of as many computers as possible. The reality is that there are now plenty of cyber-crooks on the Internet with
high levels of expertise in the latest digital fraud techniques.
Another common mistake is to think that your computer cannot possibly be of interest to Internet
criminals.
Have never used your credit card number or bank account details over the Web?
Have you never used any kind of online service -where your bank details are available- to check phone
or electricity bills? Doesn't your ISP have an area where you can edit your personal details?
Cyber-crooks know all about these things. They know that the information they want is within
reach, and all they need is the right tool to extract it. This might seem difficult, but this tool has actually been around
for a while: the Trojan.
Unlike other viruses or worms -although there are exceptions- Trojans don’t delete files, display
silly texts or even send infected emails.
Nevertheless, Trojans can steal all types of information, or let an attacker into your system,
or even give someone else complete control over your computer.
Trojans can also be used to let hackers use your Internet connection and launch attacks from
your computer.
This means that the victim of the attack will think you are responsible,
not the hacker. This technique of using PCs as 'zombies' can also link up several computers to make it even more difficult
for the real source to be detected.
To make matters worse, Trojans don't usually spread via email - as this is not subtle enough.
Often they are hidden in programs downloaded from the Internet or exploit a vulnerability to infect computers simply when
the unsuspecting user visits a website."
September 18, 2002
The amount of malicious code directed at Windows systems seems to be increasing on a continual
curve [1]. IRC bots, backdoor Trojans and worms abound.
|
|
|
(The term backdoor often refers to backdoor programs - applications that open computers for access
by remote systems. )
|
It seems that few Windows systems, particularly Win2K, are immune from infection, regardless of how diligent the user
or administrator may be.


Spyware is any technology that aids in gathering information about a person or organization without their knowledge. On the
Internet (where it is sometimes called a spybot or tracking software), spyware is programming that is put in someone's computer
to secretly gather information about the user and relay it to advertisers or other interested parties. Spyware can get in
a computer as a software virus or as the result of installing a new program.
Malicious Code :
Malicious code includes all and any programs (including macros and scripts) which are deliberately coded in order
to cause an unexpected (and usually, unwanted) event on a user's PC.
Malicious Code Trends
The speed of propagation of blended threats is increasing. For example, the Slammer worm impacted
systems worldwide in less than a few hours. Moreover, for a time, the recent Blaster worm was infecting as
many as 2,500 computers per hour. 
More than 994 new Win32 viruses and worms were documented in the first half of 2003, more than double
the 445 documented in the first half of 2002.
As the use of instant messaging clients and peer-to-peer networking increases, new worms and viruses
use these mechanisms to spread.
Of the top 50 malicious code submissions documented over the first half of 2003, 19 used peer-to-peer
and instant messaging applications-an increase of almost 400 percent in only one year.
Submissions of malicious code with backdoors has risen nearly 50
percent, increasing from 11 submissions to 17 for the first half of 2003. The most visible attempt at stealing confidential
data was the release of Bugbear.B in June 2003
.
The discovery of this variant raised serious concerns, as it specifically targeted banking
institutions.
Vulnerability Trends
Symantec documented 1,432 new vulnerabilities, a 12 percent increase over the number found in the
same period the previous year.
The number of new moderate vulnerabilities increased 21 percent and high severity vulnerabilities
increased six percent. This trend is driven by the fact that 80 percent of vulnerabilities discovered in the first half of
2003 could be remotely exploited.
Symantec reports that 70 percent of the vulnerabilities found in the first half of 2003 could be
easily exploited, due to the fact that an exploit was not required, or that an exploit was readily available.
This represents an increase of 10 percent over vulnerabilities discovered during the first half of
2002.
Symantec Internet Security Threat Report, January - June 2003
Malicious Code
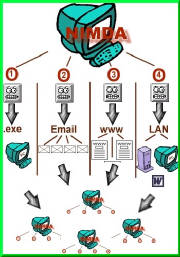
The Nimda Worm
Nimda combined many malicious code techniques into a devastating
punch that infected 2.2 million systems in its first 24 hours in the wild.
Nimda, which is “Admin” spelled backwards,
used four means of spreading (“propagation vectors,” in industry-speak):
Scanning – Nimda-infected systems scan a network
looking for unpatched Microsoft Internet Information Server (IIS) systems. Nimda then uses a specific exploit, called Unicode
Web Traversal exploit, to gain control of the target server.
Email – Nimda gathers email addresses from the mailboxes
of any MAPI-based email system. Nimda then formats messages to these addresses
using both the To: and the From: fields so the From: address will not be from the infected user.
The worm also has its own SMTP server to send out the emails, thus avoiding
Exchange or Notes servers.
When Nimda arrives in an email, it uses a MIME exploit that allows
it to execute just by reading the infected message or opening the message in a preview pane.
Browsing – Visitors to a Nimda-infected Web server
are asked to download an Outlook Express email file which contains the worm as a “readme” attachment. It then
activates using the email technique described above.
Network Shares – Nimda creates open network shares
on the target system (desktop or server), allowing complete access to that system at a later date.
After the Infection
In the past, viruses existed mainly to propagate themselves, although some were specifically
crafted to perform damage – via the delivery of their payload – to the infected system.
Hybrid threats are much more dangerous. In fact, so many servers and desktops were infected
with Nimda that the email traffic and constant scanning for new targets created a mini-"denial
of service” condition for those networks.
Typical post-infection actions include: Increasing the remote access exposure of the infected machine;
Hiding evidence of infection and removing audit trails; Placing backdoors for future unauthorized
access;
Rolling back existing security measures;
Or hiding the presence of malicious code by moving the illicit program into “stealth,”
or hibernation, mode until it is needed.
Other hybrid threat activities include clearing system logs of evidence of infection, changing file
and registry settings, reformatting or altering drives, files and data, corrupting databases, denying access to critical system
functions or applications, and enabling remote access and control of the infected host.
The hybrid, as demonstrated by Code
Red, Nimda, BadTrans, and others, is a malicious program composed of a combination of formerly
“stand alone” information security threats.
Viruses, worms, trojans and hacker techniques have been merged into automated, multi-headed attack
tools that rapidly propagate across the Internet to cause huge amounts of economic damage.
For example, Nimda infected over 2.2 million PCs and servers in
24 hours after its release to the wild in September 2001 (Computer
Economics), incurring over $530M in damages via downtime and cleanup. Code Red clocked in at an even more staggering
figure – an estimated $2.6 billion of damage.
NIMDA CODE RED CONNECTION
In
September 2001, Nimda raised new alarms by using five different ways to spread to 450,000 hosts
within the first 12 hours.
Nimda seemed to signal a new level of worm sophistication.
It found e-mail addresses
from the computer Web cache and default
Messaging Application Programming Interface (MAPI) mailbox.
Itsent itself
by e-mail with random subjects and an attachment named
readme.exe. If the target system supported the automatic execution
of embedded MIME types, the attached worm would be automatically
executed and infect the target.
It infected
Microsoft IIS Web servers, selected at random, through a
buffer overflow attack called a unicode Web traversal exploit.
It copied itself across open network shares. On an infected server, the
worm wrote Multipurpose Internet Mail Extensions
(MIME)-encoded
copies of itself to every directory, including network shares.
It added JavaScript to Web pages
to infect any Web browsers going
to that Website.
It looked for backdoors left by previous Code
Red II and Sadmind worms.
NIMDA
"The anthrax mailings and the Nimda
worm were released on exactly the same two dates.
Moreover, they were distributed via essentially the same method, and they shared a common
apparent purpose.....
Released on the Same Dates
The anthrax-laden letters were postmarked on
Sept. 18 and Oct. 9, 2001.
These are precisely the same dates that the destructive Nimda worm and a new variant
of this worm called Nimda.B were released on the Internet.
Sept. 18 was the date that the Nimda worm was released on
the Internet, and Oct. 9 was the date that the Nimda.B variant was released.
Same Method
Both involve mailing (either by the Postal Service or by e-mail) a destructive
payload to unsuspecting individuals. Although the two attacks (anthrax and Nimda)
appear at first glance to be very different from one another, a similar mind-set seems to underlie both."
"ANTHRAX-NIMDA CONNECTION"
NIMDA: Concept Virus
Released September
18 2001
September 18, 2001: The
Trenton Processing & Distribution Center processes the anthrax letters to the Editor of the New York Post and Tom Brokaw,
NBC TV. The tainted letters are postmarked Trenton, NJ, September 18, 2001.
Nimda.B is a minor variant of Nimda.A
virus that uses PUTA!!.SCR and PUTA!!.EML file names.
F-Secure Anti-Virus detects this variant with updates released
on October 9th, 2001 5:28 GMT. At that time F-secure has received no report from
affected users.
For more information on Nimda.A
please read the description:
http://www.europe.f-secure.com/v-descs/nimda.shtml
[F-Secure Corp.; October 9th, 2001]
October 9, 2001: The
Trenton Processing & Distribution Center processes the anthrax letter to Senator Daschle.
"Nimda" worm strikes Net, e-mail
Published: September 18, 2001, 5:20 PM
PDT
A computer worm that spreads to both servers and PCs running
Microsoft software flooded the Internet with data Tuesday, prompting the FBI to create a task force to investigate the attack,
sources said.
 Known as "Nimda" or "readme.exe," the worm
spreads by sending infected e-mail messages, copying itself to computers on the same network, and compromising Web servers
using Microsoft's Internet Information Server (IIS) software. Known as "Nimda" or "readme.exe," the worm
spreads by sending infected e-mail messages, copying itself to computers on the same network, and compromising Web servers
using Microsoft's Internet Information Server (IIS) software.
"It is extraordinary how much traffic this thing has created in a
couple of hours," said Graham Cluley, senior security consultant for antivirus company Sophos. "As far as we can see, it doesn't seem to be using any psychological tricks because it's all automated."

New Worm Mocks
'Billy' Gates
Reuters
08:58 AM Aug. 12, 2003 PT
A worm targeting Windows users
was spreading rapidly around the world Tuesday, triggering computer crashes and slowing Internet connections.
The worm, christened Blaster but also known as LoveSan
or MSBlaster, carried a message for Microsoft's chairman:
"Billy
Gates why do you make this possible? Stop making money and fix your software!!"
Blaster,
which zeroes in on the Windows 2000 and Windows XP operating systems, has been timed to attack a Microsoft security website
distributing the patch needed to stop the worm in its tracks before it hits millions of users.
It specifically targets the
latest versions of the Windows software and experts predict home users will be hit hardest. The vast majority of the world's
computers are equipped with one form or another of Windows software.
"I anticipate that
Blaster will have its biggest impact on the home-user community as they are more laid back about keeping their antivirus
and patches up-to-date and may have insufficient firewalls in place," said Graham Cluley, a technology consultant at Sophos
Anti Virus, a British firm.
Blaster
is fairly unusual in that it does not spread specifically by e-mail.
It can travel through
a normal Internet connection……”
http://www.wired.com/news/technology/0,1282,59987,00.html

Worm exploits a widespread Windows vulnerability
The latest worm to torment Internet users underscores the limitations of getting patches in place.
In just 24 hours, "MSBlast" exploded onto some 120,000 computers around the
world, in spite of what some experts say was a less-than-spectacular programming job. A big part of the problem was that inattentive
home users, and overbooked IT staffs, hadn't been able to put a patch in place, even though Microsoft had made it available
in July. The Web will be watching over the weekend to see if Microsoft can dodge a denial-of-service attack expected to be
launched by the worm.
MSBLAST
MSBLAST: a blast from the past:
|
VIRUS INFORMATION
Information
about the Blaster Worm
|
08/11/2003 - The Blaster worm also known as mblast, lovesan, W32.Blaster.Worm, Worm_mblast.a,
and Win32.Posa.worm. The blaster worm is a software worm designed to locate and exploit Microsoft Windows NT, Windows 2000, Windows XP, and Windows Server 2003 through open RPC ports TCP port 135. |
|
When it comes to computer vulnerabilities,
Microsoft Windows is the
swiss cheese of operating systems.
Everywhere you look there's a hole.
-Protection Technologist
| WINDOWS SECURITY |

|
| OXYMORON |
"It is indeed ironic that Microsoft requires the use of ActiveX scripting to install it's
security updates when malicious scripts - including some written in ActiveX - are being used to install malware invisibly
on millions of computers."
- Proctection Technologist
MICROSOFT
U.S. says Windows vulnerable to attack
Published: August 1, 2003, 7:46 AM PDT
"The federal government says there is new evidence that an attack is being planned on computers
using Microsoft's Windows."
"In
regards to buffer overruns, one cannot help but wonder how many of the goofs that write code for Microsoft received their
programming degrees by mail-order from Nigeria
or the Cayman Islands."
-Protective
Technologist
MICROSOFT WINDOWS VULNERABILITIES
"Microsoft programs are generally bug-free. If you visit the Microsoft hotline, you'll literally
have to wait weeks if not months until someone calls in with a bug in one of our programs. 99.99% of calls turn out to be
user mistakes."
-- Bill Gates ("Focus" Magazine)
Bugfest! Windows 2000 has 63,000
'defects'
Urging developers to clean up their code, a Microsoft exec
says: 'How many of you would spend $500 on a piece of software with over 63,000 potential known defects?'
It ships Thursday.
|
Microsoft Announces Anti-Virus Reward Program
Microsoft Teams With Worldwide Law Enforcement to Root Out Malicious Code Distributors
With $5 Million Reward Fund as a Part of Broader Security Initiative
As part of the Reward Program, Microsoft announced the first reward in the amount of a quarter-million
dollars (U.S.) for information leading to the arrest and conviction of those responsible for unleashing the MSBlast.A
worm. Although two arrests were made in connection with the B and C variants of the MSBlast worm,
those responsible for releasing the original worm this summer remain at large. The worm was designed to attack Microsoft’s
www.windowsupdate.com Web site, which provides fixes for vulnerabilities and helps protect users against malicious attacks. |
BUGS IN THE MAIL
Just as the author of the worm MSBLASTER sent a message to "Billy Gates", the author of the anthrax letters sent
a message to the "Liberal" media and two "Liberal" senators.
"It's not a great leap from mailing bugs in snail-mail to mailing
bugs in e-mail."
-Protection Technologist
SEPTEMBER 18 & OCTOBER 9
September 18, 2001: The Trenton Processing & Distribution Center processes the anthrax letters to the Editor of the New York Post and
Tom Brokaw, NBC TV. The tainted letters are postmarked Trenton, NJ, September 18, 2001.
WORM:
W32.Nimda.A@mm |
 |
| Discovered on: September 18, 2001 |
October 9, 2001: The Trenton Processing & Distribution Center processes the anthrax letter to Senator Daschle.
WORM:
W32.Nimda.B@mm |
 |
| Discovered on: October 09,
2001 |
WORM: | |
W32.Swen.A@mm |
 |
| Discovered on: September 18, 2003 |
WORM:
W32/Swen.B@mm
discovered on 9 October 2003
and is a minor variant of Swen.A, the mass-mailing worm that started spreading last month through e-mails
falsely claiming to be from Microsoft.
Swen.B is a compressed version of the original worm and is an attempt to make the worm undetectable
to some anti-virus programs. In addition to this, the majority of references within the e-mail have been changed
from Microsoft to the Italian ISP Tiscali. Otherwise the original worm and this variant are very similar.
October
9, 2001: The Trenton Processing & Distribution Center processes the anthrax letter
to Senator Daschle.
link=bacillus
Some worm and virus writers leave clues to their identities in
their coding or in some aspect of their Modus Operandi.
I-Worm.Swen
Also known as:
I-Worm.Swen (Kaspersky Lab) is also known as:
W32/Swen@MM (McAfee),
W32.Swen.A@mm (Symantec), Win32.HLLM.
Gibe.2 (Doctor Web),
W32/Gibe-F (Sophos),
Win32/Swen.A@mm (RAV),
WORM_SWEN.A (Trend Micro),
Worm/Gibe.C.1 (H+BEDV),
W32/Swen.A@mm (FRISK),
Win32:Swen (ALWIL),
I-Worm/Swen.A (Grisoft),
Win32.Swen.A@mm (SOFTWIN),
Worm.Gibe.F (ClamAV),
W32/Gibe.C.worm (Panda),
Win32/Swen.A (Eset)
The worm counts the number of computers it has infected.
It used its own hit counter at :
http://ww2.fce.vutbr.cz/bin/counter.gif/link=bacillus
.
Table 1 Cisco IOS IPS Signatures Supported in Cisco IOS Release
12.3(8)T
|
5390:0 |
Swen Worm HTTP Counter Update Attempt |
A, D, R |
SERVICE.HTTP |
Triggers when an attempt to access the URL "/bin/counter.gif/link=bacillus"
is detected. A system may be infected by the Swen worm trying the update a counter on a web page located
on the server "ww2.fce.vutbr.cz." |
Bacillus anthracis is the species of aerobic spore-forming bactera that causes anthrax disease in humans and animals.
WHAT'S IN A NAME
SWEN WORM
The worm counts the number of infected computers;
Bacillus anthracis is the species
of aerobic spore-forming bactera that causes anthrax disease in humans and animals.

"The evil genie's out of the bottle and he's a geek."
Evil Genius Virus Writter
or Script Kiddie?
You decide.

"Sven Jaschan, the 18-year-old German student named
on Monday as the author of the Sasser worm which caused havoc to computers worldwide, is an introvert who managed only a B
for computer science at high school. Yet he fits exactly the ego-driven psychological profile of the typical virus writer."
The German Boy Who Cried 'Virus' 18-year-old Sven Jaschan managed to cause up to 70% of Windows-based infections this year
The Changing Profile of the Virus
Writer
"Usually,
older virus writers work as engineers -
or system administrators in the computing
industry."
"most older writers suffer an inadequate
development of ethics"
Biological Techniques
The increasing use of genetic engineering and other molecular biological techniques
in the civilian domain means that the skills required to develop such weapons are becoming more widespread.
Larry Harris, an American Neo-nazi,
ordered three vials of bubonic plague bacteria from the American
Type Culture Collection (ATCC) which were delivered by Federal Express
He also authored a manual ‘Bacteriological Warfare:
A major threat to North America’
which is
said to be available on the Internet for $28.50 and describes not only protection from biological weapons but
also likely candidate organisms and how organisms can be grown.
BIOLOGICAL TECHNIQUES
"Anthrax spores can be produced in large quantities with basic biological techniques."
AGENTS OF TERROR
"Chemical and biological weapons are manufactured from the same chemicals and biological
techniques employed in countless pharmaceutical and biological laboratories throughout the world.
For example, products such as pesticides and fertilizers are produced from the same chemicals as
some chemical weapons - and in the case of pesticides, could be considered chemical weapons themselves".
"Black hat programmers are adapting biological and social engineering techniques to produce evermore virulent worms and viruses"
PROGRAMMING VIA BIOLOGICAL ENGINEERING TECHNIQUES
THE RETURN OF MYDOOM - MyDoom Redux: THE PROFIT MOTIVE
A new computer worm called MyDoom is spreading in the United States and abroad at a frightening rate. But that's
not the really scary news.
The worm takes possession of a computer -- either at a home or one used in business -- and turns the machine
into a remotely controlled robot programmed to send spam e-mail messages.
As if the news wasn't bad enough, there is a general suspicion the worm may contain what computer scientists
call a keystroke-logger program. If that's true, the creator of the worm can monitor every keystroke made on every infected
computer not protected by a firewall program. That provides access to everything typed, including credit card numbers and
passwords.
"I think there is a link to organized crime," Thompson said. "I don't have any proof of that, but it could easily
be. It could be harvesting credit card numbers ... or bank account log-ins."
THE PROFIT MOTIVE
BugBear.b Targets Banks Worldwide
Update: In the event a national bank thinks it is the victim of BugBear.B,
it should immediately contact its OCC portfolio manager, report the problem to law enforcement and file a SAR.
The
Bugbear.b worm has been spreading rapidly around the world over this past weekend, topping the antivirus charts as the most
prevalent virus since the Klez virus was unleashed in October. This latest varient, W32/Bugbear.B@mm, packs a particularly
nasty bite for banks.
Several virus companies and independent security firms have confirmed that buried deep within
the worm is a list of domain names for banks (xls format - text format )around the world. According to several reports, when a system is infected via email, the worm checks to see if the users domain matches any of a list of hidden
bank domains. If the Bugbear.B virus finds a match, it will keep the infected banks' workstations always online by enabling
the AutoDial feature on an infected computer through a modification the following Registry key:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings] "EnableAutodial"=dword:00000001 This
ensures that the backdoor component is accessible at all times, which makes it easier for the worm to activativate a keylogging
program that is then used to steal sensitive information.
Affecting bank computers
The worm has a large list of domains belonging mostly to banks.
At startup the worm checks the domain name of an infected computer and then compares it to the its internal list.
If the domain name matches, the worm enumerates cached passwords and sends them to a randomly selected e-mail address from
the list of addresses stored together with the corresponding SMTP server names inside the worm's body. The e-mail addresses
and SMTP server names are stored in encrypted form. This list is different from the one that the worm sends the keylogger-generated
file to.
The worm temporarily disables AutoDial feature on an infected computer by modifying the following Registry key:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings]
"EnableAutodial"=dword:00000000
After sending the files, the worm restores the key to its original value. The actions described above, make banks'
computers more vulnerable than other infected computers as stolen passwords might be used by a hacker to access infected banks'
networks from remote computers.
The list of bank domains that the worm has includes banks from many different countries:
France, UK, Germany, Australia, Italy, Greece, Denmark, New Zealand, Spain, Brasil, Romania, Poland, Argentina,
Switzerland, Finland, Taiwan, Turkey, Iceland, Slovakia, Korea, USA, South Africa, Baltic Republics, Austria, Hungary, Norway,
Czech Republic and some other countries.
1natbanker.com 1nationalbank.com 1stbk.com 1stfed.com 1stfederal.com 1stnatbank.com 1stnationalbank.com 1stnb.com
1stnewrichmond.com 1stsecuritybank.com 1stsource.com 365online.com 53.com abbeynational.co.uk abbybank.com abingtonbank.com
abnamro.be abramsbank.com abtbank.com accbank.ie acommunitybk.com adirondacktrust.com advance.com.au advance-bank.de advancefinancial.com
aea-bank.com afbank.com affinbank.com.my agfirst.com agrobresciano.it ahli.com aib.ie aibusa.com aigprivatebank.com ain.hangseng.com
alettibank.it allbank.com allbank.de allegiantbank.com alliancebank.com alliance-bank.com alpbank.com alpha.gr alpinebank.com
altapd.it amagerbanken.dk ambfinancial.com amcore.com ameribank.com american-bank.com americanbankmn.com americanbankmontana.com
americanexpress.com americanfsb.com americannationalbank.com americantrust.com amgb.com amsouth.com anb.com.sa anb.portalvault.com
anbcleveland.com anbfinancial.com anbnet.com anchorbank.com anchornetbank.com antonveneta.it anz.com.au arabank.com arjil-associes.com
arvest.com asbbank.co.nz asbonline.com ashefederal.com askbm.co.uk assbank.it assocbank.com atlanticcentral.com auburndalecoop.com
avbpgh.com avsb.com axa.be azzoaglio.it ba-ca.com baldwinfnb.com baltcosavings.com balticbankinggroup.com banamex.com bancaakros.webank.it
bancadibologna.it bancadipiacenza.it bancadirimini.it bancadisassari.it bancaetruria.it bancaintesa.it bancamarch.es bancamediolanum.it
bancaprofilo.it bancaucb.com bancavalle.it bancfirst.com bancoatlantico.es bancobrascan.com.br bancocuscatlan.com bancodisicilia.it
bancoetcheverria.es bancogalicia.com.ar bancooccidente.com.co bancopopular.com bancopopular.es bancoreal.com.br bancorio.com.ar
bancosantander.es bancosantos.com.br bancourquijo.es bancpost.ro banespa.com.br banesto.es banif.pt bank.guarantygroup.com
bank.lv bank1saar.de bank-and-trust.com bankatlantic.com bankatmbc.com bankatsecurity.com bankatunited.com bankaudiusa.com
bankcenterfirst.com bankcnb.com bankcom.com bankcsb.com bankdirect.co.nz bank-ehinger.ch bankersbankusa.com bankerstrust.com
bankeureka.com bankffs.com bankfirst.com bankgesellschaft.de bankimherzenbayerns.de bankmidsouth.com bankmidwest.com banknasb.com
banknbyc.com bankncsb.com banknewport.com banknorth.com banknorthct.com banknorthma.com banknorthvt.com banknr.com bankoa.es
bankofamerica.com bankofannarbor.com bankofbotetourtonline.com bankofclarkcounty.com bankofclarke.com bankofcleveland.com
bankofcyprus.com bankofdelmar.com bankofengland.co.uk bankoferath.com bankoffallriver.com bankofgranite.com bankofinternet.com
bankofireland.ie bankofjamestownky.com bankoflakemills.com bankofmarin.com bankofmarion.com bankofmccreary.com bankofnewglarus.com
bankofny.com bankofpetaluma.com bankofscotland.co.uk bankofthesierra.com bankofthewest.com bank-of-tidewater.com bankone.com
bankonnet.com bankorient.com bankov.com bankpds.com bankplus.com bankpnb.com bankrantoul.com bankrcb.com bank-riogrande.com
banksc.com banksnb.com bankunited.com bankwest-sd.com bankwi.com bankwmass.com banorte.com banque-de-savoie.com banquepopulaire.fr
banrbank.com banrisul.com.br banxico.org.mx barclays.co.uk barclays.pt barnatl.com basl.sk bawag.com bayernlb.de baylake.com
bayshoretrust.com bayvanguard.com bbandt.com bbbank.de bbky.com bcc.carugate.mi.it bccbrescia.it bccfc.it bccmacerone.it bccsanteramo.it
bcctriuggio.it bce.fin.ec bcee.lu bcentral.cl bcf.ch bcp.pt bcsbank.com bcv.ch bde.es belmontbank.com beneficial.com benfranklinbank.com
bes.pt bethmann-bank.de bevbank.com bfg.de bhf-bank.com bi.go.id bi.is bibank.com bics.fr bii.co.id bipop.it bischofsheimer-vb.de
biverbanca.it bkb.ch bkbank.com bkk.no bks.at blcnet.com blueridgebank.com bluestem.com blx.com bmo.com bmpro.it bnbank.com
bng.nl bnm.gov.my bnp.com.ar bnpnet-entreprises.bnpbank.com bnpparibas.com bnz.co.nz bof.fi bofm.com bogj.com boh.com bok.or.kr
boonebank.com borel.com borkenervb.de bossa.pl bot.or.th botc.com bowc.com bowmillsbank.com bp.fin.ec bpa.it bpatlantico.pt
bpci.it bpda.it bpf.it bpi.com.ph bpi.it bpic.fr bplazio.it bpm.it bpn.it bpnord.fr bportugal.pt bpr.it bpspoleto.it bradesco.com.br
bradfordbank.com bradfordfsb.com bradynationalbank.com bred.fr brentwoodbank.com bristol-west.co.uk broad-national-bank.com
broadwaybank.com broadwayfed.com brooklinesavings.com brooklynbank.com brucetonbank.com bsa.cl bsbbank.com bsi.si bsk.com.pl
bsnb.com bsp.gov.ph bsp.it bsvnet.com bundesbank.de burlbank.com busey.com business.co.uk businessbank.com bw-bank.de ca-alpesprovence.fr
ca-alsace-vosges.fr cab.it caixagalicia.es caja-granada.es cajastur.es calbanktrust.com callawaybank.com cambridgesavings.com
ca-midi.fr canajocnb.com canonbank.com ca-normand.fr capbank.com capebankonline capecodcoop.com capecodfive.com capfed.com
capitolbancorp.com capstate.com carifirenze.it carige.it caripisa.it caript.it carispfo.it carispo.it carrollbank.com carrolltonbank.com
carverbank.com cascadebank.com cashbox.de cassalombarda.it cassapadana.it cbankandtrust.com cbc.gov.tw cbnk.com cbnv.com cbolobank.com
cboviedo.com cbsbank.com cbtks.com ccbanc.com cc-bank.de ccbg.com ccbonline.com ccf.fr ccm.es centier.com central-bank.com
centralbank.net central-bank.net centralbankutah.com centralbk.com centralbnk.com centralnational.com centralstatebank.com
centreville-nat-bank.com centura.com cfbdecorah.com cfbx.com cfirst.com cfsb.com cgd.pt charterbank.com charter-bank.com charternationalbank.com
charterone.com chase.com chemicalbankmi.com chevychasebank.com chinatrust.com.tw chipbank.com chittenden.com choiceone.com
cibc.com cin.fr citibank.com citicorp.com citizensardmore.com citizensbank.com citizensbankbaytown.com citizensbankwv.com
citizensfsb.com citizenslc.com citizensnb.com citizenssavingsbank.com citizensstbank.com citizenstrust.ca citizns.com citnatbank.com
citynationalbank.com cityntl.com citywidebanks.com civibank.it civicbank.com clariden.com clevelandfed.org clevelandstatebank.com
clintonnational.com clnb.com cnbank.com cnb-brownwood.com cnbohio.com cnbsevier.com cnbt.com cnbtexas.com cnbthebank.com cnbtopekahttp
cnb-waco.com cnbwax.com coastalbanc.com coastalfederal.com coconutgrovebank.com cogeba.ch colonialbank.com coloradosbank.com
colpatria.com.co columbank.com columbiabank.com columbianbank.com combanc.com comdirect.de comerica.com commark.com commbank.com.au
commbankna.com commbanksofco.com commercebank.com commercialbank.com commerzbank.de commonwealthbank.com communitybank.com
communitybankofnaples.com communitynational.com compassbank.com compassweb.com conavi.com consumersbank.com coop-bank.com
coopcb.com co-operativebank.co.uk copiahbank.com corpbank.com corusbank.com countrybank.com countryclubbank.com countybank.com
countynationalbank.com covefi.fr cpbank.com cpbi.com cpr.fr cracantu.it crbna.com crciv.it credit-agricole.fr creditandorra.ad
credit-du-nord.fr creditlyonnais.com creditlyonnais.fr creditlyonnais.lu creditmutuel.fr credit-suisse.com crestmark.com creval.it
crosscounty.com crossplainsbank.com crownbank.com crup.it csb-bk.com csbchx.com csbiowa.com csbonline.com csbtx.com ctbnk.com
cybercmn.com danskebank.dk danverssavings.com dcbt.com deanbank.com deforestbank.com delawarenational.com dellsbank.com depfa-bank.de
deutsche-bank.de deutsche-bank-bauspar.de dewittbank.com dexia.com dexia-bil.lu dg-diskontbank.de dghyp.de digitalinsight.com
dime.com dimewill.com dit.de dnb.no dnb4you.com dollarbank.com douglascountyonline.com downeysavings.com drydenbank.com dslbank.de
dubuquebank.com dzbank.de eaglenational.com easternbank.com easternsavingsbank.com eastoncoop.com easybank.at ebankinter.com
ebankperry.net ebanregio.com ebsb.com ebtc.com edsb.com effektenbank.de efirstbank.com efsb.com egnatiasite.egnatiabank.gr
elginfc.com elmirabank.com emlakbank.com.tr empirebank.com emporiki.gr enbpb.com englewoodbank.com enterprisebank.com entrium.de
-epargne.fr equitybank.com es.ksk.de essabank.com eurobank.gr eurocardmastercard.tm.fr exchangebank.com exchangebk.com exim.com.my
exim.gov eyp.ee fabtexas.com factorypoint.com fairfieldcountysavings.com fairfieldfederal.com falkenbergs-sparb.se fallbrooknationalbank.com
falmouthbank.com farmcreditbank.com farmerssavings.com farmersstate.com farmersstatebank.com farmerstatebank.com farmerstrust.com
farmnatldan.com fbalaska.com fbr.com fbtet.com fbtmagnolia.com fcbanktn.com fcbcf.com fcb-hsv.com fcbinc.com fcbmilton.com
fcbohio.com fcbrgv.com fcbsc.com fcfbank.com fcnb.com fcsb.com fctc.com federal-bank.com ffb.com ffbnk.com ffpahomebankingonline.com
fhb.com fhlb.com fhlbc.com fhlbdm.com fhnb.com fibanc.es fibank.com fibtlink.com fidelitybank.com fidelitybk.com fidelitytopeka.com
finnat.it firstambank.com firstbankers.com firstbankingctr.com firstbank-la.com firstbankrichmond.com firstbanktexas.com firstcapitalbank.com
firstcbt.com firstcentralbank.com firstcharter.com firstcitizens.com firstcitizensnb.com firstcitizensww.com firstcitybank.com
firstclassbanking.com firstcommercebank.com firstcommunitybank.com firstcounty.com firstessex.com firstfd.com firstfedamerica.portalvault.com
firstfedbankkc.com firstfederal.com firstfederalbank.com firstfed-neib.com firstindiana.com firstinterstatebank.com firstkeystone.com
firstmd.com firstmerchants.com firstmerit.com firstmetro.com firstmidwest.com firstmountainhome.com firstnational.com firstnatlbank.com
firstnatlsc.com firstnavybank.com firstnb.com firstokmulgee.com firstsavings.com firstsb.com firstscotia.com firstsecuritybk.com
firstshorefed.com firststarbank.com firststatebanknd.com firsttennessee.com firstunited.net firstusa.com firstvirginia.com
fjsb.com fkb.ch flagstar.com flatbush.com fleet.com fmbancorp.com f-mbank.com fmbankia.com fmbanks.com fmbbank.com fmbsc.com
fmbstclair.com fmbt.com fmmarinette.com fmsb.com fmtulsa.com f-n-b.com fnbabilene.com fnbada.com fnbaltus.com fnbanksc.com
fnbanksuffield.com fnbanson.com fnbb.com fnbbank.com fnbbh.com fnbbwk.com fnb-columbia.com fnbdurango.com fnbdurant.com fnbeo.com
fnb-fl.com fnbfs.com fnbgaylord.com fnb-hampton.com fnb-hartford.com fnbimk.com fnbk.com fnbl.com fnbmd.com fnbmwc.com fnbn.com
fnbnc.com fnbnd.com fnbneg.com fnbnet.com fnbnet.net fnb-nny.com fnboa.com fnbolathe.com fnboneida.com fnbop.com fnbpipe.com
fnbportlavaca.com fnbraymond.com fnbrf.com fnb-rochelle.com fnb-scottsboro.com fnbsf.com fnb-sf.com fnbsj.com fnbt.com fnbtc.com
fnbtexas.com fnbtrenton.com fnbwalker.com fnbwaterloo.com fnbwaverly.com fnbwynne.com fnbwyo.com fncb.com foehrerbank.de fokus.no
foreningssparbanken.se fortisbank.com fortisbank.lu fortressbanks.com franklinbank.com fraspa1822.de frbsf.org fremontbank.com
friba.nl friuladria.it frostbank.com frs-l.com fsbanknet.com fsbct.com fsb-hotchkiss.com fsbme.com fsbmendota.com fsbnh.com
fsbrosemount.com fsnb.com ftbni.com fultonbank.com fvnb.com garantibank.com.tr gatewaybank.com gc4bank.com geddesfederal.com
generalbank.com genoba-meckenbeuren.rwg.de geobank.com gkb.de glacierbank.com glsb.com goldensecurity.com goleta.com goodhuebank.com
grandbank.com granitebank.com greenfieldsavings.com greenwoodsstatebank.com grsb.com grupobbva.com gruposantander.es grznord.de
gsbank.com guernseybank.com guh.de gulfbank.com habibbank.com hagerstowntrust.com halifax.co.uk hamburglb.de handelsbanken.se
hansa.ee hansa.lt happybank.com hardterraiffeisenbank.de harrisbank.com hastingscitybank.com haverhillbank.com hblsbank.com
hcsb.com hcsbank.com hdb.co.uk heartlandbank.com heartland-bank.com heidenheimer-voba.de heimstatt.de helenanational.com hellenicbank.com
heller-bank.de heritagebankna.com heritagecommunitybank.com heritagecoop.com heritagenationalbank.com hiawatha-nb.com hiberniabank.com
highpointbank.com hillsbank.com hnbank.com homebank.nbg.gr homefed.com homefederal.com homefederalbank.com homefederalsavings.com
homenational.com home-savings.com homestatebank.com homewoodfsb.com hsbc.com hsbc.com.tr humboldtbank.com huntington.com hydeparkbank.com
hypo-alpe-adria.com hypotirol.com hypovereinsbank.de iba.com.hk ibankunited.com ibercaja.es ibsc.org ibtco.com icicibank.com
ieb.hu ifsb.com ikb.de ilcommunitybank.com iltuomutuo.it imperialthrift.com inatbank.com inbursa.com.mx ing.be ingbank.nl
inlineaweb.bpm.it interamericanbank.cc interbank.com.pe intercreditbank.com interstatebank.com intrustbank.com investmentsb.com
iowabankers.com ippa.lu ipswichcoopbank.com ironbank.com isbank.is isdb.org istrobanka.sk it.ca-indosuez.com itau.com.br iwaccu.com
jacksoncountybank.com jcbank.com jeffbank.com jefferson-bank.com jeffersonstatebank.com johnsonbank.com jpbank.se jpmorgan.com
juliusbaer.com jyske-bank.dk kansasstatebank.com kawvalleybank.com kc.frb.org kearneycommbank.com kenwoodsavings.com keokuksavingsbank.com
keybank.com keystonesavingsbank.com kfb.co.kr kredytbank.com.pl ksk-alzey.de kskbb.de ksk-fds.de kskkusel.de ksk-steinfurt.de
kskwd.de kvinnherad-sparebank.no labank.com lakeareabank.com lakesstatebank.com lanb.com landesgirokasse.de lasallebank.com
laurentianbank.ca lavalsabbina.it lb.lt lbb.de lb-kiel.de lbtbank.com lbtc.com lechbank.com lefil.com legacy-banks.com lhb.de
liberty-bank.com libertysavings.com libertystatebank.com lincolnbanknc.com litimpeks.lt llb.li lloydstsb.com lnb.com lombard.co.uk
longviewbank.com lrp.de lsbank.com ls-bank.com lsbbancshares.com lvfb.com lyndonbank.com maconbank.com madbrad.com madisonbank.com
madison-bank.com maffei.de mainlandbank.com mandatum.fi mandtbank.com manubank.com marblebank.com marshallsavings.com mascomabank.com
mazobank.com mbczh.ch mbfinancial.com mbtc.com mdbank.com mdmfinancialgroup.com mechanicsbank.com mechanicssavings.com megabank.com
mercantile.net mercersavings.com merchantsandfarmers.com merchantsbankca.com merchantsbankvt.com merchantsbk.com merkur-bank.de
metbank.com metrobank.com metrobanker.com metway.com.au mfbank.com mfbonline.com mfsbank.com mhbank.com mibank.com michigannational.com
midfirst.com midsouthbank.com midstatebank.com midvalleybank.com midwestbank.com midwisc.com milfordbank.com millingtonsb.com
mkb.hu mmbank.com mohavestbank.com monitorbank.com mononabank.com monsonsavings.com montecito.com moodybank.com mps.it msbank.com
msbbank.com msbonline.com msnb.com murphywall.com myfamilybusiness.com myperrybank.com nantucketbank.com naspa.de national.com.au
nationalbank.co.nz nationalbanken.dk nationalcity.com natlbank.com natpennbank.com natwest.com nbbank.com nbcal.com nbcbank.com
nbcok.com nboc.com nbs.sk nbscnj.com nbstamford.com nbtbank.com ncb.coop ncrbanks.com nedbank.co.za netbanco.cpp.pt nettbank.fellesdata.no
netteller.com nhsb.com nkbm.si nordea.dk nordea.se nordlb.de nordlb.lv norisbank.de norrybank.com northern-bank.co.uk northernrock.co.uk
northfederal.com northview.com northwesternbank.com northwestfederal.com novabanka.hr nsbank.com nsbbank.com ntrs.com nvbank.com
nvebank.com nxbp.fr ny.frb.org obannonbank.com obb.com oberbank.at ocbc.com.sg oceanbank.com ocnb.com oeb.se oekb.co.at oekobank.de
oenb.co.at ohiobank.com ohiosavings.com olb.de oldnational.com oldpoint.com omegafinancial.com onb.com onlinebank.com onlinebankservice
orangesavingsbank.com osgv.de osuuspankki.fi ourbank.com oxford-bank.com ozarkbank.com ozkmtnbank.com pacbank.com paccrest.com
pacecu.com pacificstatebank.com paducahbank.com paffrather.de palmettobank.com parchmanvaughan.com parex.lv parishnational.com
paritate.com parkbank.com park-bank.com parknationalbank.com parkvale.com passbanca.it pastatebank.com patapscobank.com patria-finance.com
patriotbank.com paynecountybank.com pbtok.com pbz.hr pcib.com pekao.com.pl peoples.com peoplesbk.com peoplesfinancial.com
peoplesflorida.com peoplesonline.com peoplestrustco.com pffbank.com pfsb.com phil.frb.org pioneersb.com piscataqua.com pkobp.pl
planters-bank.com plymouthsavings.com pncbank.com pobank.com pointebank.com poplodi.it popso.it postabank.hu postbank.de postbank.nl
premierbank.com premiermembers.org presidential.com primebank.com priorlake.com privatbank.de providentbank.com providentbanking.com
providentbankmd.com providentnj.com providentstatebank.com providian.com psbwesthope.com psk.co.at ptsbank.com qcfb.com qcsb.com
qnb.com rabobank.de raiba-beilngries.de raiba-haibach.de raibaschleissheim.de raiffeisen.at ravallibank.com rbk-haag-gars.de
rbos.co.uk rbs.co.at rbstpoelten.at rcbank.com redriverbank.com regionalbank.com regions.com rentenbank.de republicbank.com
republicbankfl.com republictt.com reservebank.co.za rfstatebank.com rhbank.com ridgewoodbank.com rietumu.lv riggsbank.com
riversidebank.com rjbank.com rlb-tirol.at rmb.co.za rmbank.com roslynsavings.com royalbank.com rrsb.com ruralerovereto.it
ruston-rbl.com rvbank.de rvbfaktumdirekt.de rvb-fuerth.de salemfive.com salin.com salisbury-bank.com sampo.ee sampo.fi sandyspringbank.com
sanostra sanostra.es sanpaolo.it santander.de santandersantiago.cl s-b-a.com sbbgroup.com.my sbic.co.za scb.co.th scb-bc.com
scnb.com scotiabank.com scsalliancegroup.com secondnational.com secondnationalbank.com security-bank.com securitybank-decorah.com
securitybk.com securitysavings.com security-state-bank.com sella.it sequoiabank.com severnbank.com shelbybank.com signalbank.com
simmonsfirst.com sivb.com sjbank.com skandiabanken. skb.si slsp.sk smc.fr smn.no smw.at snbonline.com snoras.com snsbank.nl
socgen.com southalabamabank.com southernbank.com southfirst.com southsidebank.com southtrust.com southwestbank.com sovereignbank.com
sparda.de sparda-hh.de sparkasse- sparkasse.at sparkasse.de sparkasse.it sparnord.dk spencercountybank.com spiritbank.com
ssbnet.com ssbscott.com ssbwa.com sskm.de sssb.com stadshypotek.se standardchartered.com state-bank.com statebank-dillon.com
statebankviroqua.com statebnk.com statecentralbank.com statenb.com stearns-bank.com sterlingbancorp.com steubentrust.com stillmanbank.com
stissing.com stjohnsbank.com stls.frb.org stockexchangebank.com stonehamco-op.com stonesav.com storebrand.no stpaulbank.com
suburbanfsb.com suedwestlb.de summitbank.net superiorfederal.com susqbanc.com swbanktx.com swineford.com swiss-private-banking.com
swn-online.de synergybank.com talbot-bank.com taylorbank.com tcosouth.com td.com tdcanadatrust.com teche.com tehamabank.com
tempobank.com terrabank.com texasbank.com texasfirstbanks.com texbank.com the1st.com theabcbank.com thebank.com thebankandtrust.com
thebankoc.com thebankofelkriver.com thebankofglenburnie.com thecommbank.com thecountybank.com thefirstnationalbank.com thefsb.com
theguarantybank.com thisisyourbank.com thomastonsavingsbank.com thsbank.com tibbank.com tkb.ch tkb.lv tollandbank.com tompkinstrust.com
tradersbank.com transat.tm.fr treasurybank.com trustbank.co.nz trustcompany.com trustmark.com ttnb.com turkishbank.com txbank.com
txloanstar.com ubankal.com ubat.com ubs.com ubsh.com ucbbank.com ucbnd.com ucpb.com ufcu.com ulsterbank.com umb.com unbank.com
unibank-usa.com unicaja.es uninatbk.com union.cz unionbankvt.com unionfedbankonline.com unionplanters.com unionstate.com uniontrust.com
unitedbank.com united-bank.com unitedbank-me.com unitedbankofmichigan.com unitedbankofphiladelphia.com unitedsouthernbank.com
universalbank.com university-bank.com uob.com.sg urkb.ch usbank.com ustrustboston.com valleybank.com valleynationalbank.com
valleystatebank.com valmar.it valricostbk.com vb.lt vefbank.com venetobanca.it vibank.com vintagebank.com vobaloe.de -volksbank.de
vontobel.ch vpbank.com vr-networld.de vub.sk wachovia.com walpolebank.com walworthbank.com wanb.com warringtonbank.com washsb.com
wastbank.com watertownsavings.com watrust.com wbpr.com wcnbwooster.com webcityfed.com websterbank.com wellesleycoop.com wellsfargo.com
wellsfederalbank.com wesbanco.com westamerica.com western-bank.com westernstatebank.com westpac.com.au whisperwood.com wiese.com.pe
wilberbank.com wnsb.com wohnbausparen.at woodforest.com woodrow.mpls.frb.fed.us woolwich.co.uk woronoco.com wwsparbank.se
wyomingbank.com wyoming-bank.com yanb.com yellowstonebank.com yesbank.com ykb.com yonkers.com yosemitebank.com zhkb.ch zionsbank.com
Anthrax Plot Against Liberals?
By Reed Irvine and Cliff Kincaid | November 8, 2001
“On CNBC's Hardball show, Chris Mathews suggested the source was someone who hates liberals..”
”.. counter terrorism specialist…suspected the anthrax terrorism was domestic because
one of the letters went to Daschle, "who's on the left.”
The federal government's handling of the anthrax controversy
seems like the Keystone Cops. The most serious aspect was the failure to immediately test postal workers, two of whom died
of anthrax exposure.
Media coverage has followed confusing government statements. First, the anthrax in Senator Tom
Daschle's office was said to be "weapons-grade." Then a government scientist said it was "common-variety" anthrax. Then we
were told it was, in fact, weapons-grade.
The letters were discovered after the terror attacks of September 11th.
Some of the letters say, "Death to America," and have praise for Allah. It seems obvious to some that radical Muslims wrote
the poison letters. The letters are written or printed in such a way as to suggest they are the work of someone who has just
learned his letters and the language. That, too, suggests a foreigner who hasn't been in the U.S. very long.
But what seems obvious to some doesn't make sense to others. Gary Brown,
described as a retired Air Force counter terrorism specialist, told the Washington Post that he suspected the anthrax terrorism
was domestic because, he said, one of the letters went to Daschle, "who's on the left. If it's a home-grown militia effort,
Daschle's a likely target." But Daschle has never been a major target of the far right-wing. He's never
been seen as a major left-wing figure. One might expect the militia send a letter to an official of the Bureau of Alcohol,
Tobacco and Firearms.
Iraq has been suggested as a possible source, and this makes a lot of
sense. Iraq has concealed its hand in past terrorist incidents, such as the 1993 World Trade Center bombing. But Iraq's foreign
minister and top scientist assured Lesley Stahl on 60 Minutes that they would never do such a thing.
Following the lead of that so-called expert quoted in the Post, some of the talking heads in the media
have started suggesting that right-wingers are the source of the anthrax.
On CNBC's Hardball show, Chris Mathews suggested the source was someone who hates liberals working
at a plant making underarm deodorant.
"It's been my hunch for days now," he said, "that [the source is] some
angry person perhaps living in the New Jersey area who has been an employee of a major pharmaceutical company that may work
with aerosol sprays for underarm deodorants or whatever.
Would that kind of engineer have the capability – just because he didn't like the country, didn't
like liberals or media people, to produce this kind of anthrax and put it in an envelope?"
His guest was David Franz, the vice president of chemical and biological
defenses at the Southern Research Institute and a former commander at the Army's germ defense lab at Ft. Detrick, Maryland.
Franz politely said Mathews didn't know what he was talking about. He explained, "He'd have to learn
a lot more than just what he knew working with underarm aerosol sprays. Those are chemicals, and here we're dealing with living
things. We're dealing with a spore that you have to keep alive…
" One doesn't know whether to laugh or cry at Mathews' pathetic attempt to blame conservatives for
the anthrax terrorism.
Reed Irvine is the Publisher and Cliff Kincaid is the Editor of the AIM Report.
They can be reached at editor@aim.org.
One need neither laugh nor cry
but ponder the possibilities and
heed the clues,
as the jury's still out.
The devil is in the details.
Premise:
The Anthrax Mailer is a major Virus-Trojan- Worm writer.
Premise:
The FBI Behavioral Profile of the Anthrax Mailer is accurate.
Then
it would follow that the profile fits the Virus Writer.
Profile of the anthrax refiner/mailer:
-Ed Lake
www.anthraxinvestigation.com
1. The refiner/mailer is probably in his 40s.
2. The refiner/mailer may currently work in the health industry
or in academia.
3. The refiner/mailer has
almost unlimited access to scientific equipment and facilities.
4. The refiner/mailer probably lives within commuting distance of NYC.
5. The refiner/mailer was in the Trenton, NJ, area late on Sept. 17 and October 8, 2001.
6. The refiner/mailer probably reads the New York Post.
7. The refiner/mailer probably lives alone.
8. The refiner/mailer is probably an American citizen.
9. The refiner/mailer may have some connection to the publication
of a newsletter that expresses his beliefs.
10.
The refiner/mailer thinks that voting is a waste of time. If he belonged to a political party, it would be the Fascist
Party.
11. The refiner/mailer may be a have
mood swings between blatant egotism and deep anger.
12.
The refiner/mailer may be divorced.
13. The
refiner/mailer may have a small child and visitation rights with the child.
14. The refiner/mailer may have used his child to address the envelopes and to write the
letters.
15. The refiner/mailer may already
have published his "manifesto".
16. The refiner/mailer
probably uses the Internet frequently.
17.
The refiner/mailer may have expressed anti-Muslim sentiments during the period before the 9-11 attacks and followed that with
a lot of "I told you so" comments after 9-11. He may have expressed concerns about the number of Muslims living in Central
New Jersey.
FBI PROFILE: BEHAVIORAL ASSESSMENT
|
November 9, 2001
Amerithrax Press Briefing |
Linguistic/Behavioral Analysis of Anthrax Letters
Critical Incident Response Group
National
Center for the Analysis of Violent Crime |
Today the FBI is releasing linguistic and behavioral assessments of the person responsible for mailing anthrax-laden
letters on September 18 and October 9, 2001. We ask the American public to study these assessments and reflect on whether
someone of their acquaintance might fit the profile. The safety of the American people is at stake. If you have credible information
that might help identify this person, please contact the FBI immediately at 1-800-CRIMETV (274-6388), at www.ifccfbi.gov, or by calling your local FBI field office.
EVIDENCE DESCRIPTION
Letter 1
One page, hand-printed letter
Transmittal envelope, also similarly hand printed
Addressed
to "NBC TV – Tom Brokaw" – No return address
Postmarked Trenton, NJ 09/18/2001 (Tues.)
Letter 2
One
page, hand-printed letter
Transmittal envelope, also similarly hand printed
Addressed to "NY Post" – No return
address
Postmarked Trenton, NJ 09/18/2001 (Tues.)
Letter 3
One page, hand-printed letter
Transmittal
envelope, also similarly hand printed
Addressed to "Senator Daschle – 509 Hart Senate Office Building"
Return
address – "4th Grade, Greendale School, Franklin Park, NJ"
Return address zip code – "08852"
Postmarked
Trenton, NJ 10/09/2001 (Tues.)
LINGUISTIC ASSESSMENT
It is highly probable, bordering on certainty, that all three letters were authored
by the same person. Letters 1 and 2 are identical copies. Letter 3, however, contains a somewhat different message than the
other letters. The Anthrax utilized in Letter 3 was much more refined, more potent, and more easily disbursed than letters
1 and 2.
In the past, the public has helped the FBI solve high profile investigations that involved writings by coming forward to
identify the author, either by how he wrote or by what he wrote. We are asking for the public's help here again in the same
way.
While the text in these letters is limited, there are certain distinctive characteristics in the author's writing style.
These same characteristics may be evident in other letters, greeting cards, or envelopes this person has written. We hope
someone has received correspondence from this person and will recognize some of these characteristics.
The characteristics include:
1. The author uses dashes ("-") in the writing of the date "09-11-01." Many people use the slash ("/") to separate the
day/month/year.
2. In writing the number one, the author chooses to use a formalized, more detailed version. He writes it as "1" instead
of the simple vertical line.
3. The author uses the words "can not," when many people prefer to spell it as one word, "cannot."
4. The author writes in all upper case block-style letters. However, the first letter of the first word of each sentence
is written in slightly larger upper case lettering. Also, the first letter of all proper nouns (like names) is slightly larger.
This is apparently the author's way of indicating a word should be capitalized in upper case lettering. For whatever reason,
he may not be comfortable or practiced in writing in lower case lettering.
5. The names and address on each envelope are noticeably tilted on a downward slant from left to right. This may be a characteristic
seen on other envelopes he has sent.
6. The envelopes are of the pre-stamped variety, the stamps denoting 34 cents,
which are normally available directly from the post office. They are not the traditional business size envelopes, but the
smaller size measuring approximately 6 1/4" x 3 ½".
BEHAVIORAL ASSESSMENT
Based on the selection of Anthrax as the "weapon" of choice by this individual, the offender:
• is likely an adult male.
• if employed, is likely to be in a position requiring little contact with the public, or other employees. He may
work in a laboratory. He is apparently comfortable working with an extremely hazardous material. He probably has a scientific
background to some extent, or at least a strong interest in science.
• has likely taken appropriate protective
steps to ensure his own safety, which may include the use of an Anthrax vaccination or antibiotics.
• has access to a source of Anthrax and possesses knowledge and expertise to refine it.
• possesses or has access to some laboratory equipment; i.e., microscope, glassware, centrifuge, etc.
• has exhibited an organized, rational thought process in furtherance of his criminal behavior.
• has a familiarity, direct or indirect, with the Trenton, NJ, metropolitan area; however, this does not necessarily
mean he currently lives in the Trenton, NJ, area.. He is comfortable traveling in and around this locale.
• did not select victims randomly. He made an effort to identify the correct address, including zip code, of each
victim and used sufficient postage to ensure proper delivery of the letters. The offender deliberately "selected" NBC News,
the New York Post, and the office of Senator Tom Daschle as the targeted victims (and possibly AMI in Florida). These targets
are probably very important to the offender. They may have been the focus of previous expressions of contempt which may have
been communicated to others, or observed by others.
• is a non-confrontational person, at least in his public life. He lacks the personal skills necessary to confront
others. He chooses to confront his problems "long distance" and not face-to-face. He may hold grudges for a long time, vowing
that he will get even with "them" one day. There are probably other, earlier examples of this type of behavior. While these
earlier incidents were not actual Anthrax mailings, he may have chosen to anonymously harass other individuals or entities
that he perceived as having wronged him. He may also have chosen to utilize the mail on those occasions.
• prefers being by himself more often than not. If he is involved in a personal relationship it will likely be of
a self serving nature.
Pre-Offense Behavior
• Following the events of September 11, 2001, this person may have become mission oriented in his desire to undertake
these Anthrax mailings. He may have become more secretive and exhibited an unusual pattern of activity. Additionally, he may
have displayed a passive disinterest in the events which otherwise captivated the Nation. He also may have started taking
antibiotics unexpectedly.
Post-Offense Behavior
• He may have exhibited significant behavioral changes at various critical periods of time throughout the course
of the Anthrax mailings and related media coverage. These may include the following;
1. Altered physical appearance.
2. Pronounced anxiety.
3. Atypical media interest.
4. Noticeable mood swings.
5.
More withdrawn.
6. Unusual level of preoccupation.
7. Unusual absenteeism.
8. Altered sleeping and/or eating habits.
These
post-offense behaviors would have been most noticeable during critical times, including but not limited to: the mailing of
the letters (09/18/01 and 10/09/01), the death of first Anthrax victim, media reports of each anthrax incident, and especially
the deaths and illnesses of non-targeted victims.
AGAIN, IF YOU HAVE CREDIBLE INFORMATION THAT MIGHT HELP IDENTIFY THIS PERSON, PLEASE CONTACT THE FBI IMMEDIATELY
AT 1-800-CRIMETV
(274-6388), AT WWW.IFCC.FBI.GOV, OR BY CALLING YOUR LOCAL FBI FIELD OFFICE.
# # # |
|
|
ANTHRAX: FBI BEHAVIORAL PROFILE
|

